Pre-deployment Requirements
Before you begin, check that you meet the following prerequisites to ensure a smooth installation process.
Installation Overview
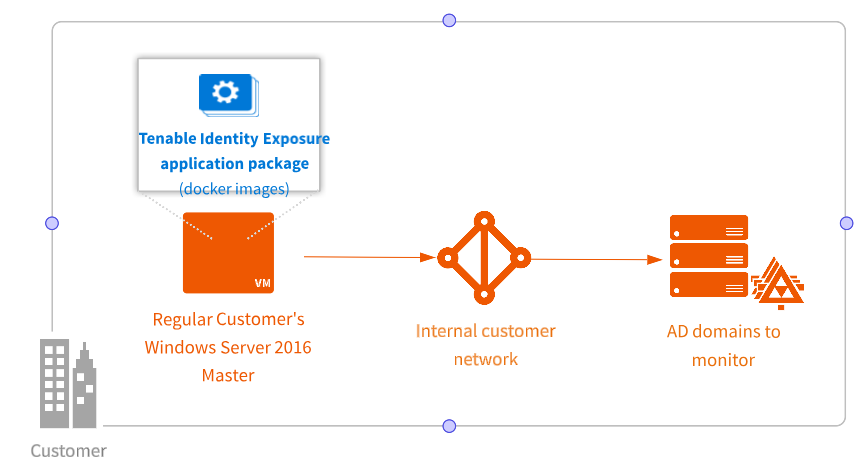
You install Tenable Identity Exposure as an application package hosted in a dedicated Windows environment that must fulfill specific hosting specifications.Tenable Identity Exposure requires access to the operating system's master image on the system where you install it.
Tenable preconfigures the application package with only Tenable services and your specific requirements. This deployment option offers maximum flexibility and integrates seamlessly into your specific environment.
Tenable Identity Exposure runs on a micro-services architecture embedded into Windows services. These services have a dedicated purpose (storage, security analysis, application, etc.) and all are mandatory. Consequently, you can only install Tenable Identity Exposure on operating systems supporting the micro-services model.
TLS Certificates
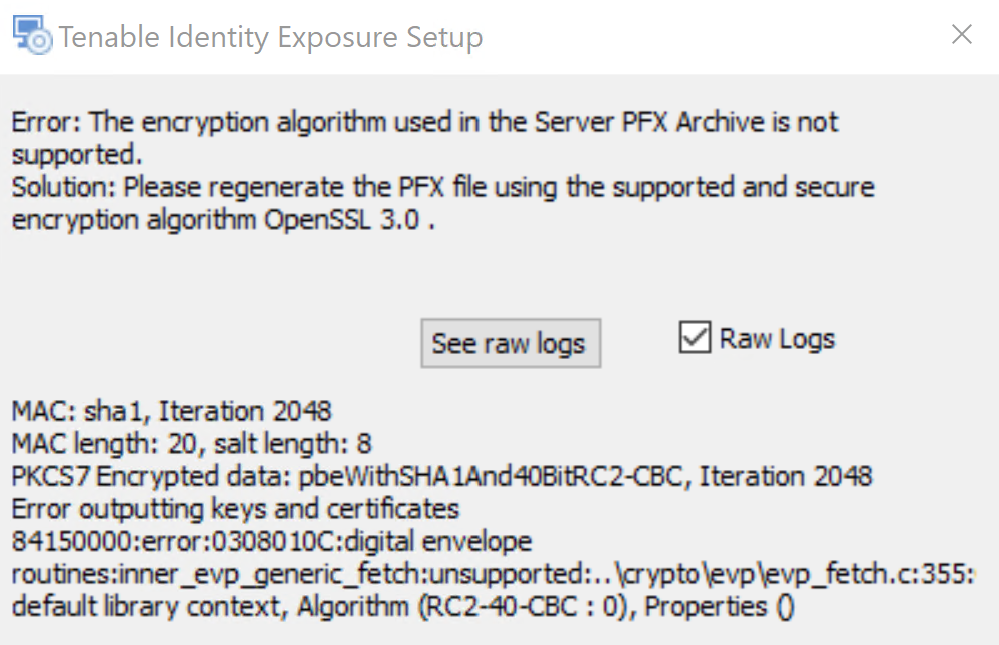
OpenSSL 3.0 Support — Starting with version 3.59.5, Tenable Identity Exposure uses OpenSSL 3.0.x. As a result, X.509 certificates signed with SHA1 no longer work at security level 1 or higher. TLS defaults to security level 1, which makes SHA1-signed certificates untrusted for authenticating servers or clients.
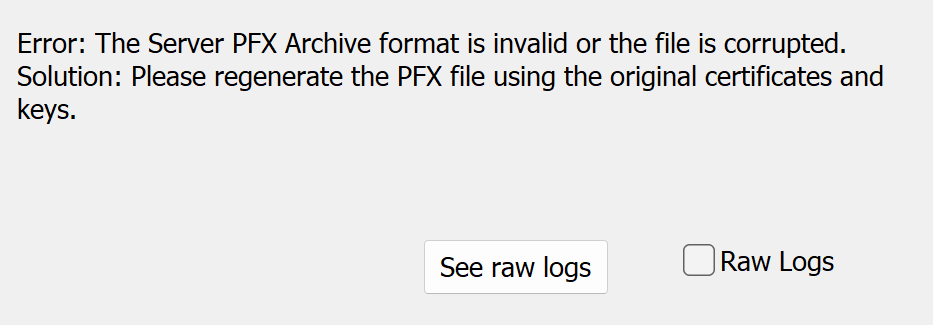
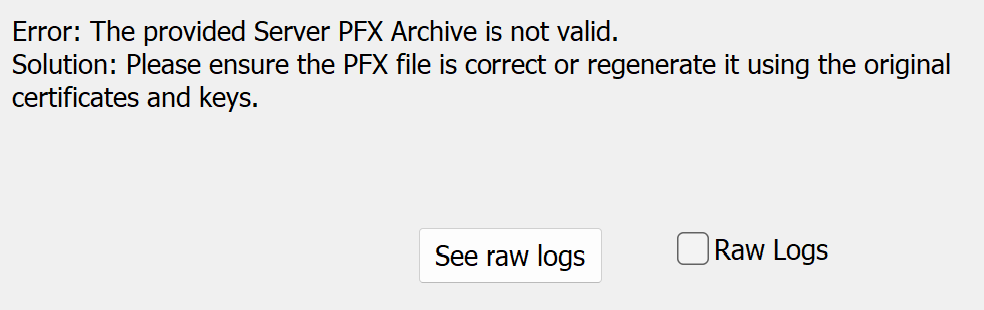
You must upgrade your certificates in response to this change. If you continue the installation without updating your certificates to use OpenSSL 3.0, the Tenable Identity Exposure installer returns the following error messages with recommended fixes:
Account Privileges
Perform the installation as the local account member of the local or built-in administrators group or as an administrator on the server where you install Tenable Identity Exposure.
Caution: Log in to the machine as this local administrator account outside the domain. Do not log in as a local administrator within the domain.
The account requires the following permissions:
-
SeBackupPrivilege
-
SeDebugPrivilege
-
SeSecurityPrivilege
Antivirus (AV) and Endpoint Detection and Response (EDR)
Before installing, disable any AV and/or EDR solution on the host. Failing to do so triggers a roll-back during installation. You can safely enable AV/EDR once the installation is complete, but be aware that it may impact product performance due to high disk I/O operations. See also "Unsupported Configurations" below.
File Path Exemptions for Security Node Engine
Create the following file exemptions for Erlang:
-
%PROGRAMFILES%\Tenable\Tenable.ad\SecurityEngineNode\rabbitmq_data: Full directory exemption
-
%PROGRAMFILES%\Erlang OPT\*\bin\epmd.exe
-
%PROGRAMFILES%\Erlang OPT\*\bin\erlsrv.exe
-
%PROGRAMFILES%\Erlang OPT\*\bin\erl.exe
Note: Use '*' as a wildcard because the directory name changes with every Erlang version upgrade.
Example: %PROGRAMFILES%\Erlang OPT\erts-14.2.5.11\bin\erl.exe
File and Process Allowlist
To install Tenable Identity Exposure successfully in a restricted on-prem environment, you must allow specific application files. Exclude the following files and directories to ensure smooth installation and runtime performance:
| Component/Path | Reason |
|---|---|
| AppDir C:\Tenable\Tenable.ad Note: "C" is the default installation folder; your installation folder may differ. |
Contains the main application files. Antivirus or EDR can block the application from starting. |
|
Erlang Env:ProgramFiles\Erlang OTP RabbitMQ Env:ProgramFiles\RabbitMQ Server |
Handles communication between services; may disrupt RabbitMQ services. |
|
Env:windir\System32\config\systemprofile\.erlang.cookie Env:UserProfile\.erlang.cookie |
Used for RabbitMQ authentication; may prevent services from connecting or authenticating with each other. |
| IIS w3wp.exe | Hosts the Web application; may slow down response times or timeouts. |
|
Node Env:ProgramFiles\nodejs dotnet Env:ProgramFiles\dotnet |
Runtime environments; engines running Tenable services. |
|
SQL Env:ProgramFiles\Microsoft SQL Server Exact SQL paths depends on your installation: <SQL UserDB Disk> <SQL UserDB Log Disk> <SQL TempDB Disk> |
May slow queries or cause database corruption. |
Pending Reboots
Perform any required reboots prior to installation. When you launch the installer on a server, it checks the following:
-
There is no pending reboot.
-
The server was restarted properly less than 11 minutes ago.
-
The MSI checks the following registry keys:
-
HKLM: \ Software \ Microsoft \ Windows \ CurrentVersion \ Component Based Servicing \ RebootPending
-
HKLM: \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ WindowsUpdate \ Auto Update \ RebootRequired
-
HKLM: \ SYSTEM \ CurrentControlSet \ Control \ Session Manager -> PendingFileRenameOperations
-
Service Accounts
The use of service accounts must be allowed on the operating system.
Note: This service account must be able to read all object attributes.
Indicators of Attack
The Windows event log must have a minimum retention time of 5 minutes to ensure the application can accurately retrieve all events.
Unsupported Configurations
The following table details unsupported configurations:
|
Configuration |
Description |
|---|---|
|
Active anti-virus or Endpoint Detection and Response (EDR) solution |
The Tenable Identity Exposure platform requires intensive disk I/O.
|
|
Firewalls |
Do the following to allow Tenable Identity Exposure services to communicate with each other to have reliable security monitoring:
|
|
Erlang |
|
Third-Party Applications
Deploying Tenable Identity Exposure’s platform in a non-certified environment can create unexpected side effects.
In particular, the deployment of third-party applications (such as a specific agent or daemon) in the master image can cause stability or performance issues.
Tenable strongly recommends that you reduce the number of third-party applications to a minimum.
Access Rights
Tenable Identity Exposure’s platform requires local administrative rights to operate and ensure a proper service management.
-
You must provide the Tenable technical lead with the credentials (username and password) associated with the administrative account of the host machine.
-
When deploying to a production environment, consider a password renewal process that you validate jointly with the Tenable technical lead.
Product Updates
As part of its upgrade program, Tenable frequently publishes updates to its systems to provide new detection capabilities and new product features.
-
In this deployment, Tenable only provides updates for Tenable Identity Exposure components. You must ensure a proper management of your operating systems, including the frequent deployment of security patches. For more information about Tenable Identity Exposure releases, see the Tenable Identity Exposure Release Notes.
-
Tenable Identity Exposure's micro-services architecture supports the immediate application of operating system patches.
Other Requirements
-
Tenable Identity Exposure works with Windows Servers listed in Hardware Requirements with the latest available update.
-
Tenable Identity Exposure installation program requires Local Administrator rights on Windows Server 2016 or later. If the account used for the installation is the default account, ensure that this account can run programs without restrictions.
-
Tenable Identity Exposure services require Local Administrator rights to run local services on the machine.
-
Tenable Identity Exposure requires a dedicated data partition. Do not run Tenable Identity Exposure on the OS partition to prevent system freeze if the partition is full.
-
Tenable Identity Exposure SQL instance requires the virtual accounts usage feature.
-
When installing or upgrading Microsoft SQL Server after implementing tighter security measures, the installation process fails due to insufficient user rights. Check that you have the necessary permissions for a successful installation. For more information, see the Microsoft documentation.
-
Tenable Identity Exposure must run as a black box. Dedicate each machine to Tenable Identity Exposure and do not share it with another product.
-
Tenable Identity Exposure can create any folder starting with the ‘Alsid’ or ‘Tenable’ prefix on the data partition. Therefore, do not create folders starting with "Alsid" nor "‘Tenable" on the data partition.
-
Erlang: Do not modify the HOMEDRIVE environment variable. The PATHEXT environment variable must contain the .exe and .bat file extensions.
-
If you must set the AD service account of Tenable Identity Exposure as a Protected Users group member, ensure your Tenable Identity Exposure configuration supports Kerberos authentication, because Protected Users cannot use NTLM authentication.
Pre-installation Checklist
This table resumes the prerequisites in a handy checklist before installation.
|
Information or Resource to Reserve |
Status |
|---|---|
|
The required agreements (NDA, Evaluation Software License), if applicable. |
|
|
The number of active AD users in the targeted domains to monitor. |
|
|
The computing and memory resources are based on Tenable Identity Exposure’s sizing matrix. See Resource Sizing. |
|
|
The private IP of each virtual machine used to deploy Tenable’s platform. |
|
|
The type and IP address of the update management infrastructure, the time server, PKI server, and identity provider. |
|
|
Open required network flows for each service that Tenable Identity Exposure requires. See Network Flow Matrix. |
|
|
The private IP addresses of each Primary Domain Controller emulator. |
|
|
Creation of a regular user account on each Active Directory forest to monitor. |
|
|
On the specific Active Directory containers, grant access right to the Tenable service account. |
|
| Grant access for Privileged Analysis if you want to enable this feature. | |
|
The AD domain user account login:
|
|
|
A TLS certificate issued for Tenable Identity Exposure’s Web Portal issued from the customer’s PKI
|
|
|
The list of Tenable Identity Exposure user accounts to create:
|
|
|
The list of optional configurations to activate (email notification, Syslog event forwarding, etc.) |
|
|
An identified and available project coordinator to work with Tenable. |
|
|
Technical staff to respond to potential technical issues such as network filtering issue and unreachable PDCe. |
See also